Exchange Zero days are very common these days and there is a freshly baked one today (30th September 2022 as of writing). If you want to know what how the vulnerabilities work, take a look at the reference at the bottom. As a sysadmin I care about securing my systems.
Here are a few steps to mitigate this zero day vulnerability:
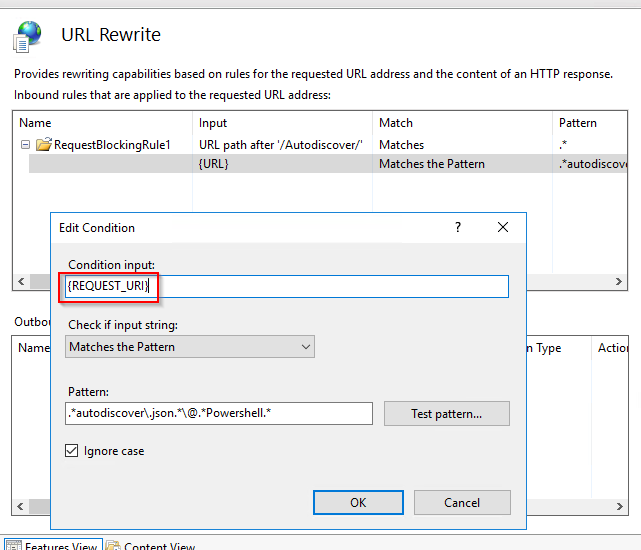
In IIS Manager on the Exchange Server, select the Autodiscover virtual directory and open URL Rewrite and add a new rule.
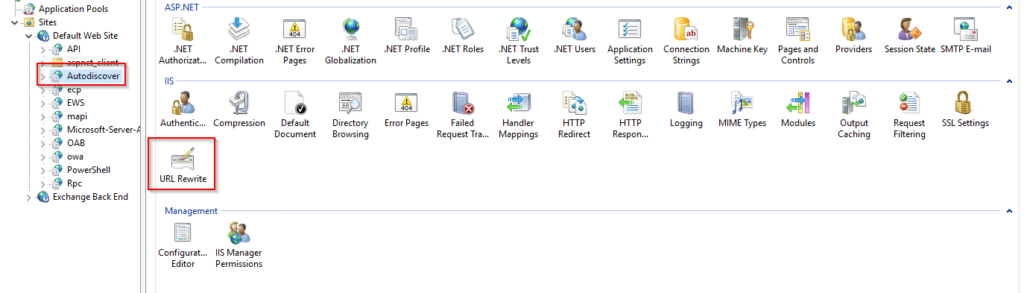
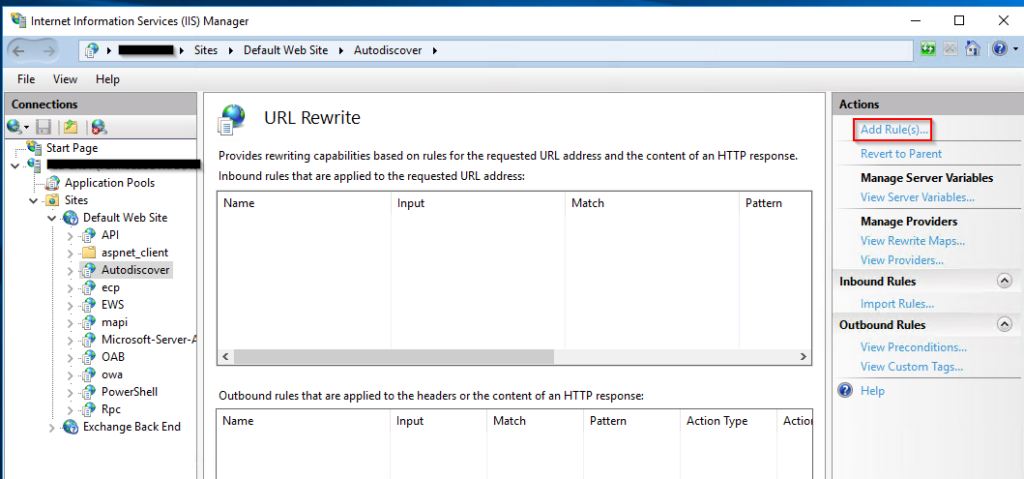
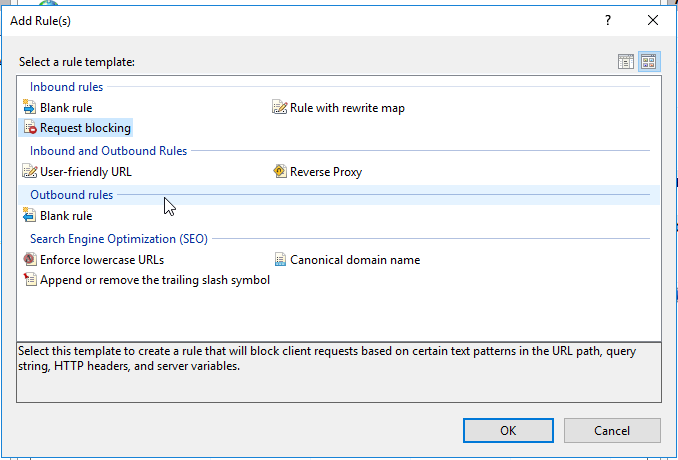
Select Request Blocking
Enter the string
.*autodiscover\.json.*\@.*Powershell.*
Using should be changed to Regular Expression.
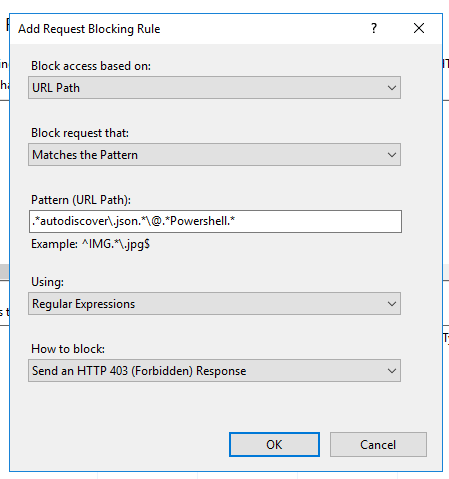
Change URL to REQUEST_URI and save the changes.
References:

On our Exchange Server 2016 CU 19 server, if I look in Default Web Site -> Autodiscover I do not have a URL Rewrite option.
Does that mean we are not vulnerable?
Exchange 2016 CU19 is pretty old. I would strongly suggest to update to the newest CU, which is CU23. I am pretty sure in one of the newer CUs IIS Rewrite Module/URL Rewrite has to be installed.
Thank you, Ajni. I will start by patching to CU 23.
You are welcome!