Azure VM Sizes are very confusing and there are a lot of them that seem very similar. This website helps you compare VM sizes with each other, showing you price/performance ratio etc.
Reading time: 1 min
Azure VM Sizes are very confusing and there are a lot of them that seem very similar. This website helps you compare VM sizes with each other, showing you price/performance ratio etc.
If you are having this error with an Excel file saved in SharePoint Online being stuck at “Performing Cleanup” when closing the file, this fix might help you. Also, the file is somehow cached locally and does not update with the current online version of the file. Onedrive reset also does not help.
Empty this folder:
%localappdata%\Microsoft\Office\16.0\OfficeFileCache
This might also help you:
If you are getting this error when trying to login to Microsoft 365 Apps, this fix might help. The error says “Your computer’s Trusted Platform Module has malfunctioned. Error Code 80090034.
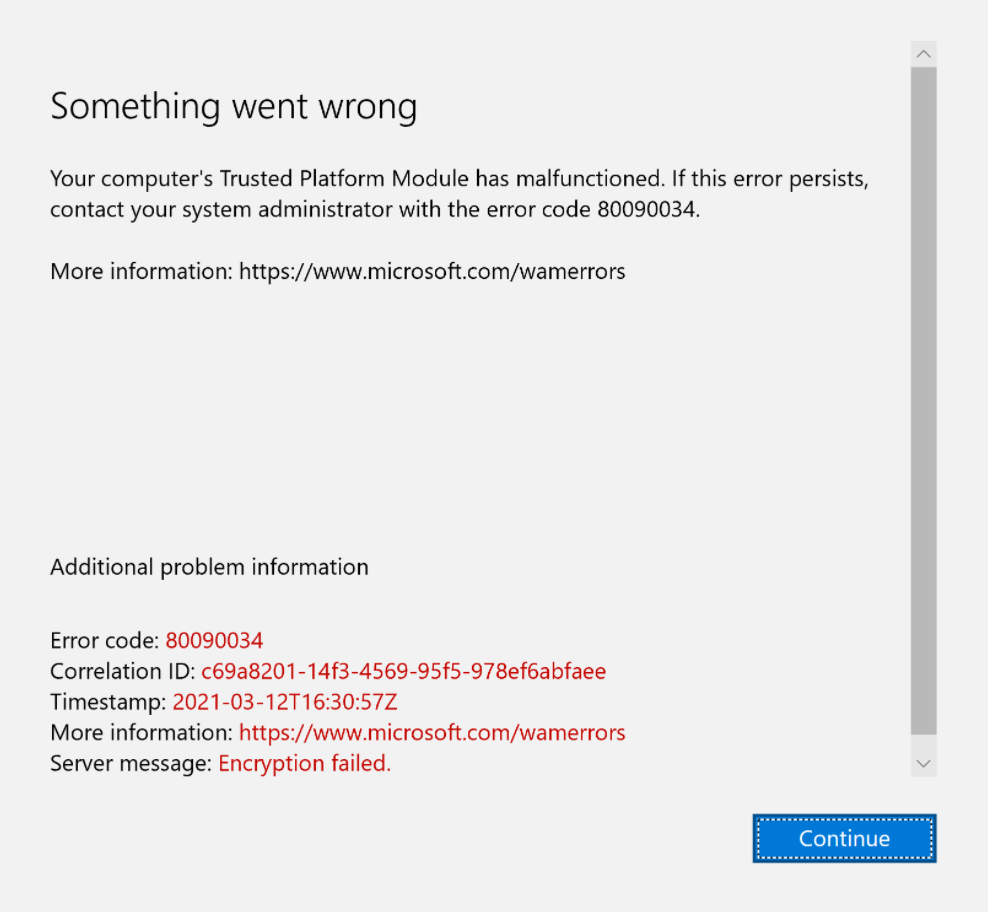
To fix that, configured this registry key/value:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Protect\Providers\df9d8cd0-1501-11d1-8c7a-00c04fc297eb
DWORD Protectionpolicy 1
The value 1 indicates a specific setting, but without direct documentation from Microsoft, the precise effect of 1 on this policy isn’t readily available. It typically refers to enabling or enforcing a particular cryptographic protection policy, possibly related to password protection or other cryptographic functions in Windows.
This was tested on Windows 10.
This Monday, 13th of January 2025 was a bad day for sysadmins. Outlook and other Microsoft 365 / Office Apps would crash upon start because of a new update pushed by Microsoft. The message says something about react-navis-win32.dll missing. The only fix is to install the December 2024 Updates to fix the issue.
This configuration XML File install the December 2024 updates. Beware: This configuration is for Windows Server 2016 RDS and note that automatic updates are disabled.
<Configuration ID="e2abcd00-6229-40cc-be2d-e3a8ff5efb34">
<Add OfficeClientEdition="32" Channel="Broad">
<Product ID="O365BusinessRetail">
<Language ID="de-de" />
<Version ID="16.0.17328.20670"/>
<ExcludeApp ID="Groove" />
<ExcludeApp ID="Lync" />
<ExcludeApp ID="OneDrive" />
<ExcludeApp ID="Teams" />
</Product>
</Add>
<Property Name="SharedComputerLicensing" Value="1" />
<Property Name="SCLCacheOverride" Value="0" />
<Property Name="AUTOACTIVATE" Value="0" />
<Property Name="FORCEAPPSHUTDOWN" Value="FALSE" />
<Property Name="DeviceBasedLicensing" Value="0" />
<Updates Enabled="FALSE" />
<RemoveMSI />
<Display Level="None" AcceptEULA="TRUE" />
</Configuration>To download data hit setup.exe /download configuration.xml
To install execute setup.exe /configure configuration.xml
References:
If you want to publish your Web App to the internet, you ideally should not directly NAT port 443 (or you custom HTTPS port) to you internal server. Instead, there should be a Reverse Proxy in a DMZ that accepts requests and then routes them to the internal server. You need to configure a Reverse Proxy with nginx or IIS.
Here is how you can do it with IIS.
Install IIS Role in Server Manager (Add Roles and Features > Web Server (IIS)
Download and install URL Rewrite and Application Request Routing (ARR)
https://iis-umbraco.azurewebsites.net/downloads/microsoft/url-rewrite
https://iis-umbraco.azurewebsites.net/downloads/microsoft/application-request-routing
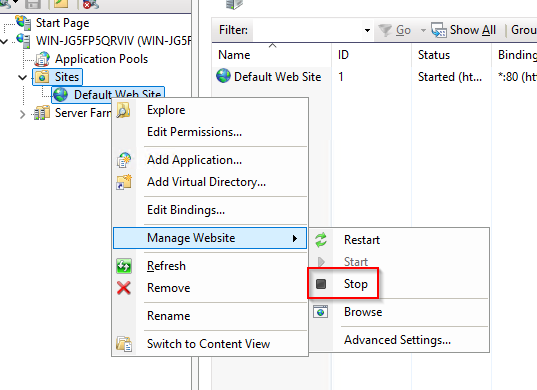
In IIS Manager, stop Default Website:
Create a new Website:
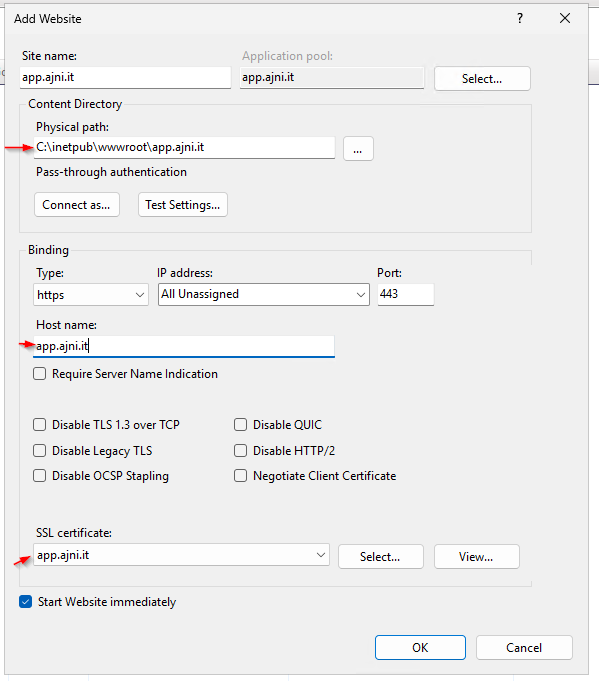
Make sure you configure your parameters. The host name should be the public DNS name.
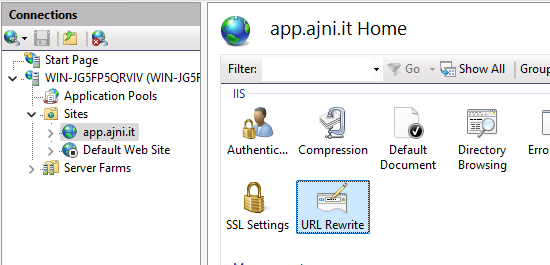
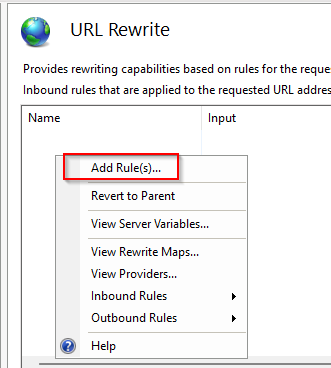
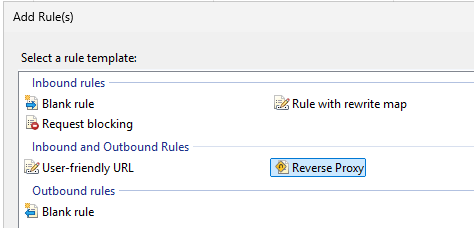
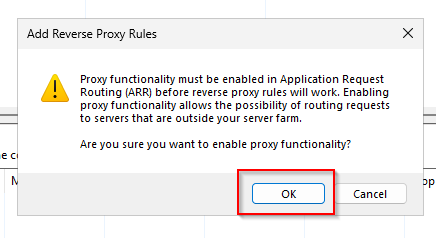
Now open URL Rewrite and create a new rule.
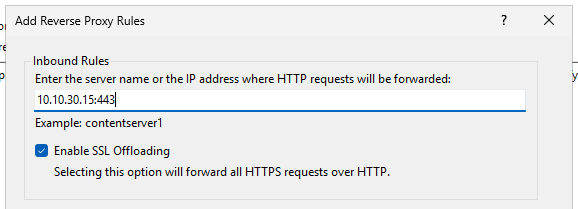
Enter the ip of the internal server along with the port.
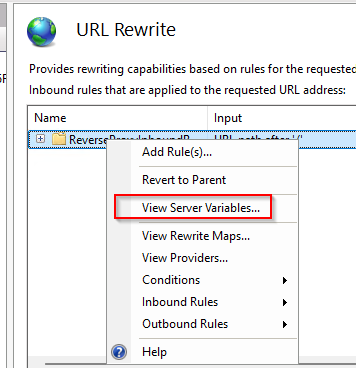
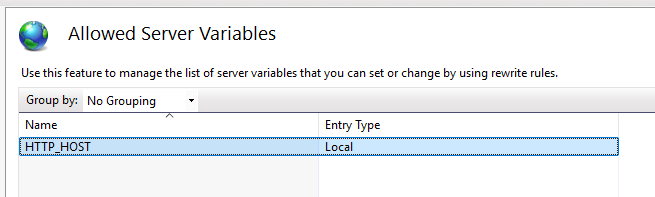
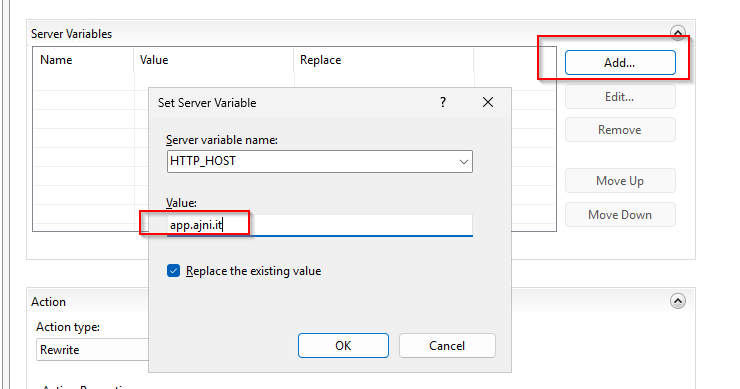
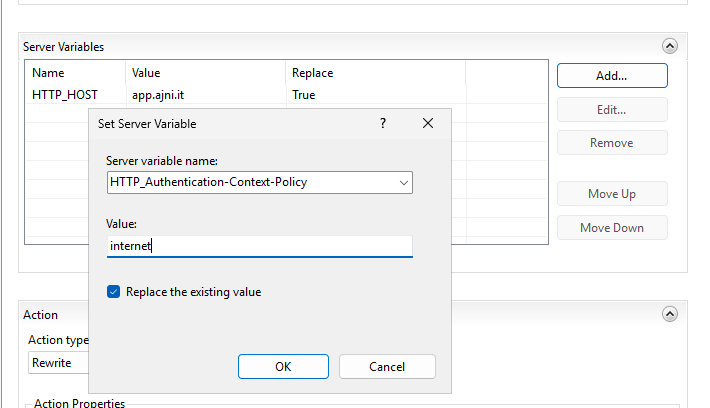
View Server Variables and add HTTP_HOST and HTTP_Authentication-Context-Policy as a variable.
Go back to rules and double click on the rule you just created.
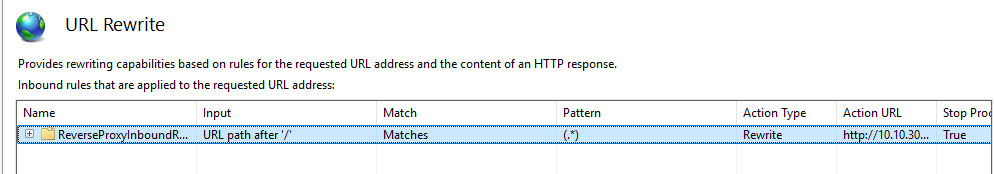
Open server variables and add the application’s host name under HOST_NAME.
Add another variable with the name HTTP_Authentication-Context-Policy and value of internet
You should have variables.
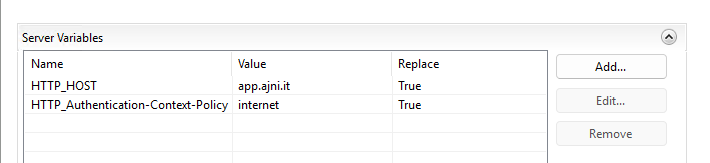
Apply settings at the top right.
Next, select the server and open Configuration Editor:
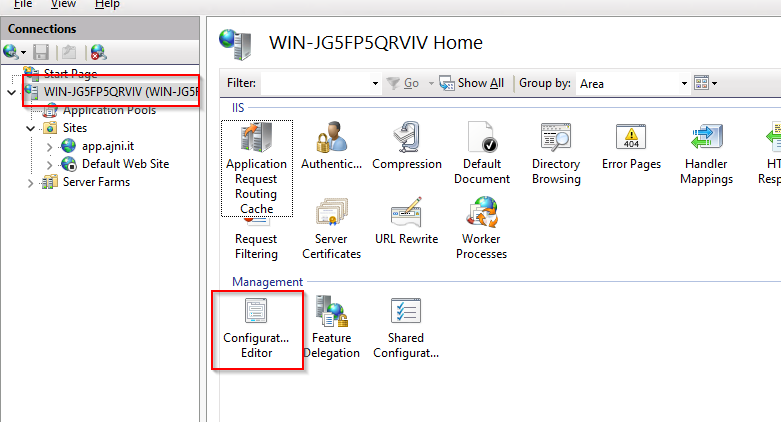
Go to section System.Webserver/Proxy
Set preserveHostHeader to true and reverseRewriteHostInResponseHeaders to false
Apply changes at the top right.
Bonus: Increase timeout if bigger data chunks are sent to the client.
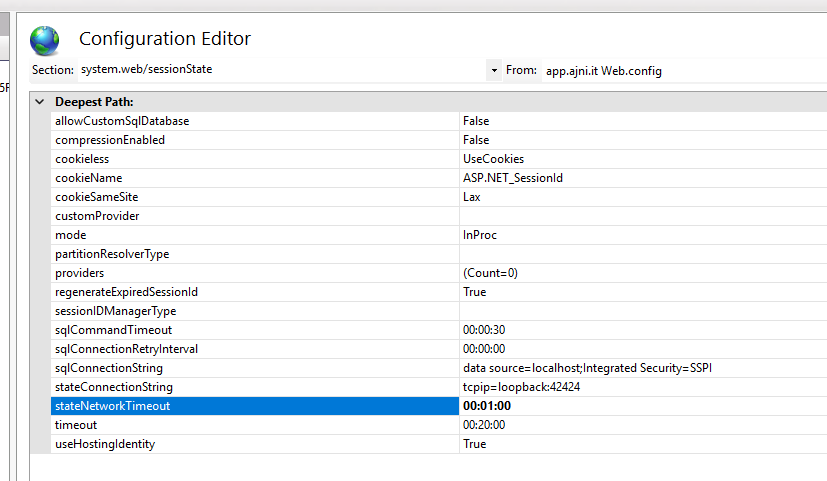
On the site, open Configuration Editor
Open Section system.web/Sessionstate
In stateNetworkTimeout increase value to 01:00 or higher.
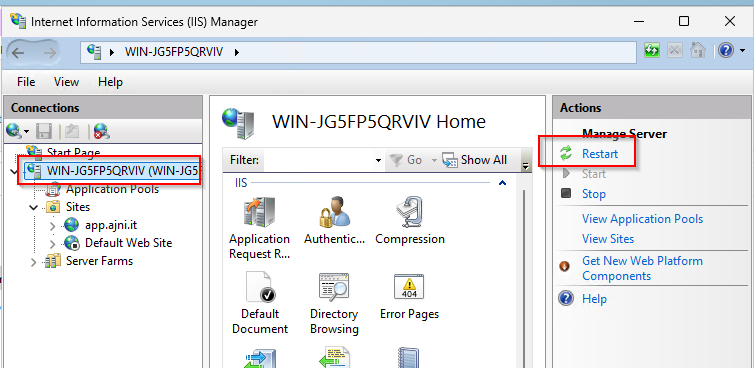
Don’t forger to apply changes and restart IIS.
Like what you are reading? Buy me a coffee.
